The Cybersecurity Maturity Model Certification (CMMC) is a critical framework for businesses that work with the Department of Defense (DoD). It ensures that contractors and subcontractors meet essential cybersecurity requirements to protect controlled unclassified information (CUI). CMMC readiness and gearing up for compliance may seem complex, but with the right approach, your business can take proactive steps to achieve certification without feeling overwhelmed.
Understanding the CMMC Framework and Its Importance
CMMC is designed to safeguard sensitive federal contract information by ensuring that companies handling this data implement necessary cybersecurity practices. The framework consists of multiple levels, each representing a different degree of security maturity. Contractors must comply with the CMMC level specified in their contracts to remain eligible for DoD opportunities.
Key Steps to Achieve CMMC Readiness
Businesses can take several actions to prepare for CMMC compliance. While third-party security assessments are required at certain levels, organizations can take proactive steps to ensure they meet the standards well in advance.
1. Identify Your Required CMMC Level
Every contractor must determine which CMMC level applies to their operations. This information is typically outlined in contract requirements. The levels range from basic cybersecurity hygiene to advanced security protocols.
2. Conduct a Gap Analysis
Performing a self-assessment allows businesses to evaluate their existing cybersecurity practices against CMMC requirements. This involves:
- Identifying security gaps in policies and technical controls.
- Reviewing compliance with NIST 800-171, which forms the foundation of CMMC Level 2.
- Documenting any deficiencies and areas needing improvement.
3. Develop and Implement a Plan of Action
After identifying gaps, businesses should create a structured plan to address them. This should include:
- Strengthening access controls and authentication measures.
- Enhancing data encryption for stored and transmitted information.
- Improving incident response plans to detect and mitigate threats.
- Establishing employee training programs on cybersecurity best practices.
4. Maintain an Accurate System Security Plan (SSP)
An SSP outlines how a company protects CUI and maintains cybersecurity hygiene. A well-documented SSP is essential for proving compliance during an assessment. Companies should regularly update their SSP to reflect changes in security measures and evolving threats.
5. Ensure Regular Security Monitoring
Continuous monitoring of IT systems is crucial for maintaining cybersecurity. Businesses should:
- Deploy security information and event management (SIEM) tools.
- Conduct periodic vulnerability assessments and penetration testing.
- Establish incident reporting mechanisms to respond to cyber threats efficiently.
What Are the Different CMMC Levels?
CMMC compliance is divided into different levels, each with distinct security requirements:
Level 1 (Self-Assessment)
- Requires implementation of 15 security controls outlined in FAR clause 52.204-21.
- Annual self-assessments conducted by the organization seeking assessment (OSA).
- Results must be entered into the supplier performance risk system (SPRS).
- No plan of action and milestones (POA&M) is permitted.
Level 2 (Self-Assessment)
- Requires compliance with 110 security controls from NIST SP 800-171 R2.
- Self-assessment must be conducted every three years.
- Businesses must document results in SPRS.
- POA&Ms are permitted within 180 days to close gaps.
- Affirmation is required annually to maintain compliance.
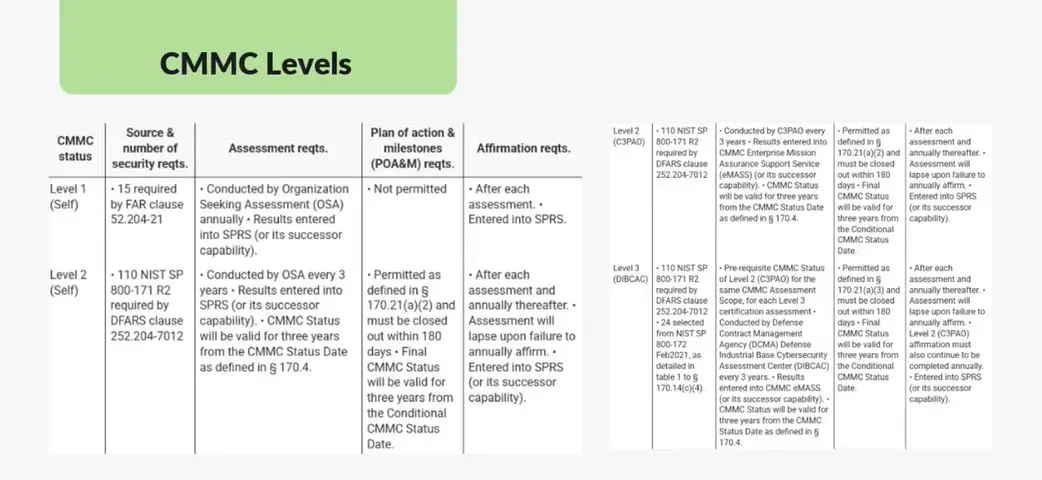
Level 2 (C3PAO-Assessed)
- Also based on 110 NIST SP 800-171 R2 controls.
- Assessment must be conducted every three years by a certified third-party assessor organization (C3PAO).
- Results are recorded in the CMMC enterprise mission assurance support service (eMASS).
- POA&Ms are allowed with a 180-day remediation window.
- Annual affirmation is required to maintain status.
Level 3 (DIBCAC-Assessed)
- Builds on Level 2 but introduces additional security requirements.
- Requires an advanced cybersecurity program:
- 24 selected controls from NIST SP 800-172.
- Contract Management Requirement (DIBCAC) assessment.
- Assessment is required every three years.
- POA&Ms are permitted within 180 days.
- Annual affirmation is required to maintain compliance.
Best Practices for CMMC Compliance
To stay ahead of CMMC requirements, businesses should follow these best practices:
✔ Stay Informed
Keep up with changes in DoD regulations and cybersecurity frameworks.
✔ Train Employees
Provide regular cybersecurity training to reduce risks of human error.
✔ Document Everything
Maintain clear documentation of policies, security controls and remediation efforts.
✔ Implement Strong Cybersecurity Measures
Use multi-factor authentication, data encryption tools and endpoint security to protect sensitive data.
✔ Conduct Internal Audits
Regular self-assessments help ensure continuous compliance.
Final Recommendations for CMMC Readiness
CMMC compliance is a necessary step for businesses working with the DoD. While the process may seem challenging, taking a structured approach to self-preparedness can make it more manageable. By identifying the required CMMC level, conducting thorough self-assessments and implementing best practices, your business can strengthen its cybersecurity posture and ensure long-term compliance.
You can proactively approach CMMC preparedness and navigate the compliance process with confidence and efficiency.
Contact Afidence and gain the expertise you need to close analysis gaps, assess your current infrastructure and strengthen your defenses to ensure CMMC compliance requirements are met. Start your CMMC preparedness journey today.

